Did you realize that your Confidential Information and Computer Systems are constantly at risk of an attack?
Published by Inn-FinIQ | 12th August 2022 | Cyber-security, Types of attacks, Need for security, Security Environment, Ethical Hacking, Top 10 attacks, Cyber-security Statistics, Cyber-threats, Cyber-safety tips.

Importance of Information Security
- The cost of cybercrime would grow by 15% p.a. over the next five years to reach $10.5 trillion by 2025. (Cyber-security Ventures)
- There are 1,053,468 people employed in cyber-security as of February 2022 in the U.S. (Cyber Seek)
- The cost of phishing attacks amounts to $17,700 every minute. (CSO Online)
- 68% of the business leaders feel their cyber-security risks are increasing. (Accenture)
- Approximately 70% of total breaches in 2021 were financially motivated. (Verizon)
Cyber-security
Also known as IT security/Electronic Security; cyber-security involves protecting the systems, networks, programs, devices, and data from malicious attacks. The company may use certain technologies, processes, and controls for protection.
Cyber-security vs. Information Security
Information security is especially about protecting the data which are either electronically or physically stored whereas cyber-security involves protecting data stored in electronic form from being attacked.

Cyber-threats
Cyber-threats are deliberate acts performed with harmful intentions such as stealing data, causing damage or losses, and disrupting computer systems (Obotivere & Nwaezeigwe, 2020). These attacks could be classified as Cybercrimes which intend for financial gain or cause disruption; Cyberattacks, motivated by information gathering; and Cyberterrorism intended to cause panic and fear (P.S.Seemma, et al., 2018).
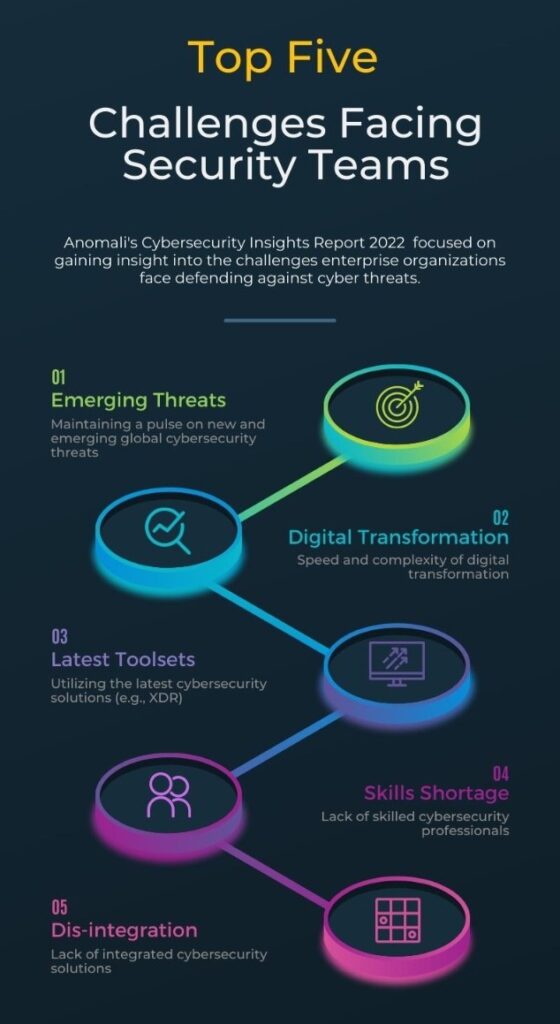
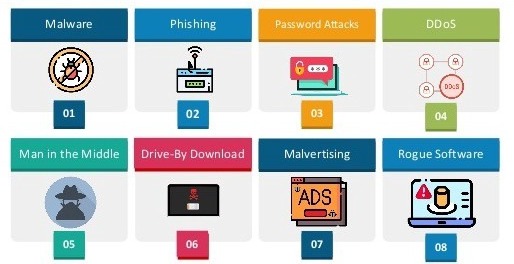
Types of Cyber attacks

Hi, I am Gnanadarshana Maduranga
I am an IT professional and am in charge of cyber-security in my company. I have experience in developing cyber-security systems and policies for corporates.

Types of Cyber attacks
Cyber-threats are deliberate acts performed with harmful intentions such as stealing data, causing damage or losses, and disrupting computer systems (Obotivere & Nwaezeigwe, 2020). These attacks could be classified as Cybercrimes which intend for financial gain or cause disruption; Cyberattacks, motivated by information gathering; and Cyberterrorism intended to cause panic and fear (P.S.Seemma, et al., 2018).
As a result of the significant increase in cyber-attacks around the world; it is extremely important to protect your confidential information, devices, systems, and networks from these malicious attacks. Around 95% of the breaches occur as a result of human errors (Mee & Brandenburg, 2020). Simple actions such as updating the software and operating systems, use of anti-virus software, strong passwords, being cautious with email links and attachments, and avoiding unsecured Wi-Fi networks.
Ethical Hacking
It is the process of detecting vulnerabilities in
a system, application, or data (Maurushat, 2019).
In simple it is about testing the vulnerabilities
of a secured computer system by imitating
a malicious hacker.

Benefits of Cyber-security
The main benefits of cyber-security include;
01. Prevent financial fraud and loss.
02. Enforce Confidentiality, Integrity, and Availability.
03. Ensure business continuity and customer confidence.
04. Protection of Intellectual Property.
05. Prevents damage to hardware

Conclusion
It is extremely critical that all organizations take necessary action for data and cyber-security as modern organizations are highly dependent on information and technology in their business activities (Pande, 2017). Failure to take such action could lead to loss of confidential information, legal issues such as GDPR, financial losses, reputational impact, and even the survival of the company could be at stake. Hence all organizations should develop and implement cyber-security policies and strategies to protect their information and systems.
Author
INN-FINIQ Team
References
Maurushat, A., 2019. Ethical Hacking. Ottawa: University of Ottawa Press [Accessed 01 August 2022].
Mee, P. & Brandenburg, R., 2020. World Economic Forum. [Online]
Available at: https://www.weforum.org/agenda/2020/12/cyber-risk-cyber-security-education [Accessed 02 August 2022].
Obotivere, B. A. & Nwaezeigwe, A. O., 2020. Cyber Security Threats on the Internet and Possible Solutions. International Journal of Advanced Research in Computer and Communication Engineering, 9(9), pp. 92-97 [Accessed 01 August 2022].
P.S.Seemma, S.Nandhini & M.Sowmiya, 2018. Overview of Cyber Security. International Journal of Advanced Research in Computer and Communication Engineering, 7(11), pp. 125-128 [Accessed 02 August 2022].
Pande, J., 2017. Introduction to Cyber Security. s.l.:Uttarakhand Open University [Accessed 01 August 2022].